Have you ever wondered how companies, researchers, or privacy fans change their online identity without being tracked? Distorting proxies offer a smart solution to mask, redirect, and modify network traffic, keeping browsing safe and giving user control over how web servers see requests. This article breaks down what distorting proxies actually are, why they matter today, and how real-world data proves their effectiveness.
What is a Distorting Proxy?
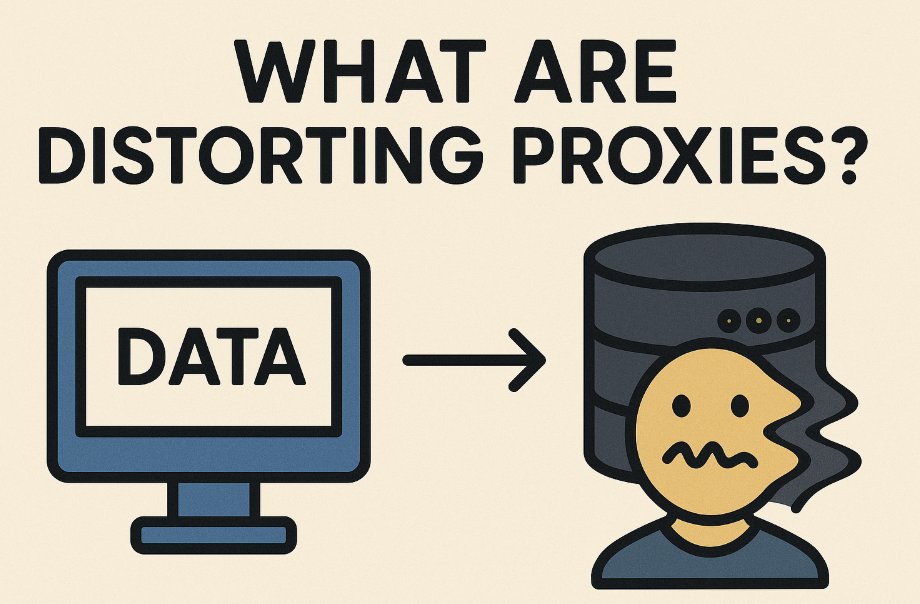
Distorting proxies act as middlemen that intentionally modify (“distort”) information in web requests sent from your device to target websites. Unlike traditional proxies that just hide your IP, distorting proxies can:
- Change request headers (such as the “User-Agent”)
- Modify cookies and referer fields
- Shift geo-location info
- Mask your real network fingerprint
By reshaping how requests appear, these proxies help users evade tracking, access region-blocked content, and avoid detection on websites that check for suspicious activity.
Proxy Types and Features:
🏘️ Rotating Residential Proxies
How Distorting Proxies Work
When you browse through a distorting proxy, your online traffic first goes to the proxy server. Here’s what happens:
- The proxy intercepts the request and strips or modifies key fields.
- It might swap out your IP address with another, change user-agent tags, or edit metadata fields.
- The website you visit sees a different source: the altered request, not your real one.
Typical Uses for Distorting Proxies
- Data scraping for SEO and market research
- Accessing blocked or geo-restricted websites
- Social media automation
- Ad verification and review monitoring
- Testing applications and cybersecurity controls
Discover our (use case):
Benefits of Distorting Proxies
Distorting proxies are popular for a reason. Here’s why they’re favored in web scraping, research, and privacy:
- Hide your true location: Servers see the proxy’s IP, not yours
- Avoid blocks and CAPTCHA: Distorted headers help bypass anti-bot checks
- Flexible targeting: Change country, region, and device fingerprints on the fly
- Enhanced privacy and safety: Keep activity untraceable and secure
Even big brands use distortion proxies for fraud detection and ad testing.
Distorting Proxy Technology Explained
Most distorting proxies operate through specialized server-side logic. The modern market is dominated by:
- Rotating Residential Proxies: Millions of real-user IPs, automatically rotated for each request.
- Static Residential Proxies: Dedicated “real” IPs for longer sessions.
- Mobile and Datacenter Proxies: Unique fingerprints for app-based or high-volume scraping.
Common Applications in Business and Research
Distorting proxies aren’t just for privacy fans, they power serious business workflows.
- Review Monitoring: Companies check customer reviews across countries, undetected.
- Ad Verification: See exactly how ads display in different regions.
- Travel Fare Aggregation: Collect prices globally with location tricks.
- Cybersecurity: Test for vulnerabilities without exposing real infrastructure.
The Rise of ‘Ethically Sourced’ Proxy Networks in 2025
In 2025, there’s a surge in demand for privacy tools, but ethical sourcing matters. Distorting proxies from trusted vendors offer:
- Ethically sourced IPs: No “zombie” botnets, only real user traffic
- 99.9% uptime and ultra-fast response: Supports large-scale data collection
- Detailed usage stats: Dashboard tools to monitor your bandwidth and users
Security and Legality: Fast Facts
Using distorting proxies is legal in most regions, as long as activities stay within website’s terms of service. Modern providers offer:
- HTTP/SOCKS5 security: For safe, encrypted connections
- Dedicated support: 24/7 chat teams, account managers for enterprises
A word of caution: avoid using proxies for harmful or unauthorized activity. Always choose reputable providers and read their compliance policies.
How ProxyEmpire Stands Out
ProxyEmpire is a premium proxy service provider designed to empower web scraping, data collection, and unrestricted internet access through a vast network of ethically sourced residential, mobile, and datacenter proxies. Below is a detailed description based on the provided information:
Overview of ProxyEmpire
ProxyEmpire offers a comprehensive suite of proxy solutions tailored for individuals, businesses, and developers seeking reliable, high-performance tools for data gathering, privacy protection, and bypassing geo-restrictions. With over 9.5 million clean IP addresses spanning 170+ countries, ProxyEmpire provides unparalleled global coverage, ensuring users can access content at scale with a 99.9% uptime and lightning-fast response times (as low as 0.6 seconds).
Proxy Types and Features:
🏘️ Rotating Residential Proxies
Key Benefits
- Global Reach: Access to over 9.5 million IPs worldwide, covering every major region, with precise targeting options (country, city, state, ASN/ISP).
- High Reliability: A 99.86% uptime ensures uninterrupted service, supported by patented technology for enhanced speed and security.
- Ethical Sourcing: Proxies are responsibly harvested, ensuring quality and compliance.
- Versatile Use Cases: Supports web scraping, price monitoring, sneaker copping, SEO tracking, ad verification, and more.
- Integration-Friendly: Compatible with standard proxy protocols (HTTP, SOCKS5) and third-party tools like Multilogin, Dolphin Anty, Kameleo, Octobrowser, and Gologin.
- No Hidden Fees: Transparent pricing with all features included, starting at a $1.97 trial.
Use case:
Why Choose ProxyEmpire?
- Massive Proxy Pool: Over 9.5 million IPs, outpacing competitors with broader coverage and quality.
- Superior Performance: High success rates (up to 99.95% for scraping) and industry-leading speeds.
- User-Friendly: Intuitive dashboard, developer-friendly documentation, and 24/7 support with dedicated account managers for corporate clients.
- Cost-Effective: Flexible pricing with no limits on concurrent sessions and a rollover data feature unique to ProxyEmpire.
FAQ:
What is a distorting proxy?
A distorting proxy is a type of proxy server that masks a user’s real IP address by substituting it with a false or “distorted” IP address in the HTTP headers. Unlike transparent proxies, which reveal the user’s IP, or high-anonymity (elite) proxies, which hide both the IP and the fact that a proxy is being used, distorting proxies provide a middle level of anonymity. They identify themselves as proxies to the target server but present a fake IP address to conceal the user’s true location and identity.
How does a distorting proxy work?
When a user sends a request to access a website, the request is routed through the distorting proxy server. The server modifies the HTTP headers, specifically fields like “X-Forwarded-For” or “Via,” replacing the user’s real IP address with a false one. The target website receives the request, perceiving it as coming from the fake IP address, and sends the response back to the proxy, which then relays it to the user. This process helps conceal the user’s true IP and location while still indicating that a proxy is in use.
What are the main uses of distorting proxies?
Distorting proxies are used for various purposes, including:
- Anonymity: They hide the user’s real IP address, enhancing privacy during online activities.
- Bypassing Geo-Restrictions: By presenting a false IP from a different location, users can access content restricted to specific regions, such as streaming services or news websites.
- Web Scraping: They help avoid IP bans by masking the user’s IP, making it harder for websites to detect and block automated scraping tools.
- Caching: Distorting proxies can cache frequently accessed data, reducing load times and bandwidth usage.
- Security: They add a layer of protection against cyber threats by concealing the user’s real IP from malicious websites or hackers.
How does a distorting proxy differ from other proxy types?
- Transparent Proxies: These do not hide the user’s IP address and openly identify as proxies, often used for content filtering but offering no anonymity.
- Anonymous Proxies: These hide the user’s IP but identify as proxies to the target server, providing more anonymity than transparent proxies but less than distorting proxies.
- High-Anonymity (Elite) Proxies: These hide both the user’s IP and the fact that a proxy is being used, offering the highest level of anonymity. Distorting proxies, while anonymizing the IP, still reveal that a proxy is in use.
- Residential Proxies: These use real IP addresses from actual devices, making them harder to detect than distorting proxies, which use fake IPs.
What are the benefits of using a distorting proxy?
- Enhanced Privacy: Masks the user’s real IP, reducing the risk of tracking or data exposure.
- Access to Restricted Content: Allows users to bypass geo-restrictions for streaming, research, or accessing censored content.
- Improved Web Scraping: Enables data collection without triggering IP-based blocks.
- Caching Efficiency: Stores frequently accessed data to improve browsing speed and reduce bandwidth usage.
- Protection on Public Networks: Shields the user’s IP when using unsecured Wi-Fi, such as in coffee shops or airports.
What are the drawbacks of using a distorting proxy?
- Detectability: Since they identify as proxies, some websites may block them, limiting access to certain content.
- Performance Impact: Routing traffic through a proxy can slow down connection speeds due to additional processing and distance.
- Reliability Issues: Free or low-quality distorting proxies may be unreliable, slow, or already blacklisted by websites.
- Limited Anonymity: Unlike high-anonymity proxies, they don’t fully conceal that a proxy is being used, so advanced tracking methods may still identify the user.
- Legal and Ethical Risks: Misusing proxies for activities like violating website terms or local laws can lead to bans or legal consequences.
How do distorting proxies compare to VPNs?
- Anonymity: Both mask the user’s IP, but distorting proxies only anonymize web requests and don’t encrypt traffic, while VPNs encrypt all internet traffic for higher security.
- Security: VPNs offer stronger protection due to encryption, making them better for sensitive activities like online banking.
- Use Cases: Distorting proxies are ideal for web scraping or bypassing geo-restrictions, while VPNs are better for overall privacy and secure browsing.
- Performance: Proxies may be faster for specific tasks like scraping, as they don’t encrypt data, but VPNs provide a more secure connection at the cost of some speed.
Who should use a distorting proxy?
Distorting proxies are suitable for:
- Individuals: Seeking to browse anonymously, access geo-restricted content, or protect their IP on public Wi-Fi.
- Businesses: Conducting web scraping, market research, or ad verification while maintaining anonymity.
- Journalists or Activists: Accessing censored content or protecting their identity in regions with internet surveillance.However, for highly sensitive tasks requiring full anonymity, high-anonymity proxies or VPNs may be more appropriate.
Can websites block distorting proxies?
Yes, some websites can detect and block distorting proxies because they identify themselves as proxies in HTTP headers. Rapid proxy rotation, where a new IP is used for each request, can help mitigate this by making it harder for websites to analyze and block the proxy. Choosing a reputable provider with a large pool of IPs can also reduce the likelihood of blocks.