When you want privacy or anonymity on the internet, the first thing you should do is
hide your IP Address. Your IP Address can be easily traced back to you and used as a way to gain knowledge of your location.
The article below will teach you how to keep yourself hidden from anyone who
tries to track your activities.
What Is An IP Address?
First, let’s talk a little bit about what an IP Address is.
What you need to know is that it’s a unique number assigned to your computer from an internet service provide every time you connect to the internet.
That means no two people have the same IP Address and most likely yours can be traced back to you if someone wants to find out who you are or where you live.
In fact, just by reading an article like this article on your laptop or smartphone, platforms can already trace your IP Address and tell right where you’re sitting. That’s a scary thought, but don’t worry—we have a quick and easy solution for you.
Let’s Take A Look At a Few Ways To Hide Your IP Address
Method #1 Residential & Mobile Proxies
Proxies by definition are simply an object between you and the platform you are connecting to. They work by giving you an assigned IP Address from a real internet service provider or in the case of mobile proxies, a phone carrier.
Unlike free proxies which leak your real IP Address, backconnect proxies do not reveal your information to the web assets you visit.
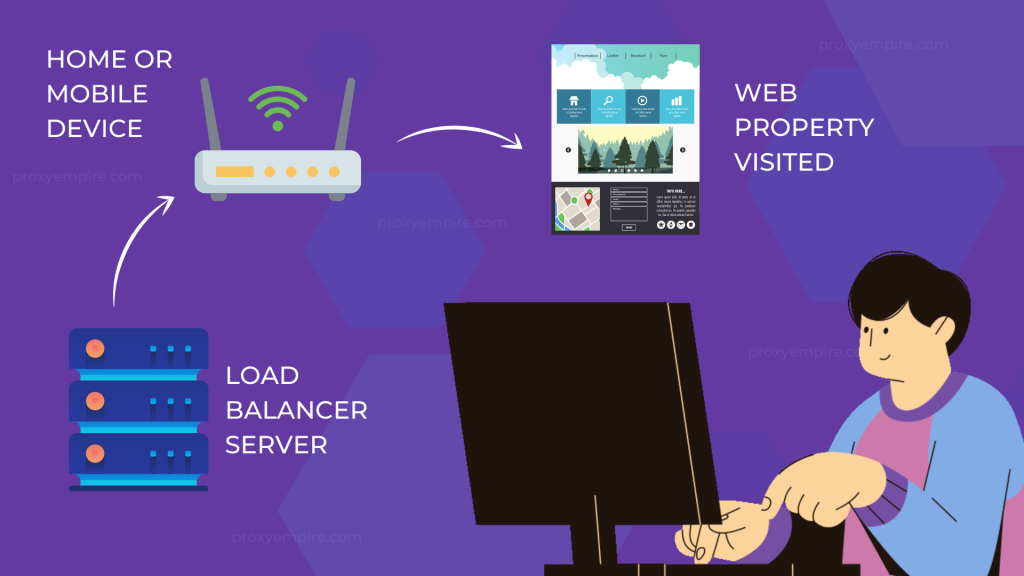
As with any tech, it is important to choose a proxy partner such as ProxyEmpire that does not keep logs, accepts payments with respect to privacy, and gains access to people’s devices with 100% legal compliance.
Datacenter-sourced proxies come from large server warehouses that are only available in big cities, whereas residential & mobile proxies (Backconnect) are widespread throughout the world because they’re sourced from real devices.
Finally, to get the most from your proxies you should separate your browser fingerprint by using anti detect software or divided browser profiles.
You can start using a proxy in under 3 minutes with our Chrome integration tutorial.
Method #2 Virtual Private Servers
The first is called the “Virtual Private Network” also known as a VPN. What a VPN can do for you is reroute all your Internet traffic through an external server, so instead of seeing your computer’s IP Address, anyone looking will see the address of the server you go through.
What this does is encrypt all of your data so if anyone is trying to follow your Internet connections, it will be extremely difficult for them.
A VPN also masks your physical location and in most cases, you can pick a new one that will fool anyone who tries to track you.
In the past, it was fairly difficult to find a good VPN, but today there are so many available that you should have no trouble finding one. What you need to do is read through their privacy policy before buying anything because some of them can collect logs on what you do while using them.
Logs invalidate the purpose of a VPN by shifting all of your personal data
into the hands of the VPN company.
Be careful!
Some VPNs (APPs Especially) have fine print that gives them access to your internet network so that they can rent it out to clients. This is one method large proxy companies use to gain
access to your devices.
Method #3 TOR
The other method is referred to as TOR or The Onion Router. What this does is bounce your connection around through multiple machines so instead of it being traced back to you, it’s bounced around until there are so many traces that it gets lost in the mix.
When you use TOR, your IP Address is hidden through “onion routing” which is a method where data packets are sent through a network of relays before reaching their destination.
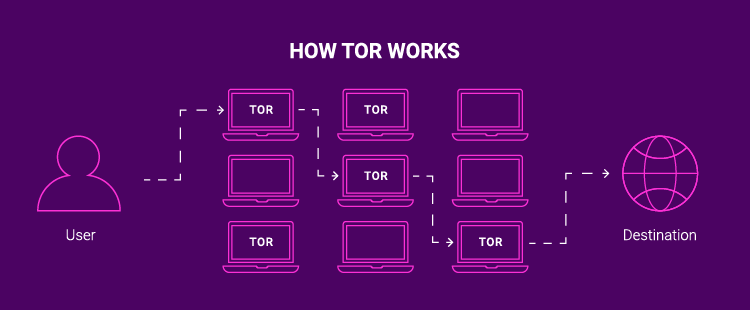
While this happens, someone trying to trace it will only get snippets of data since it’s changed so many times before getting to its final connecting point.
You can enhance your anonymity by installing and utilizing the TOR browser.
What you need to know is that TOR can be slow at times, but it’s usually worth the wait when you’re looking for absolute privacy with anonymity on the Internet. Web platforms can also know you’re using TOR and block your connection.
Let’s Wrap It Up
Now you have three powerful ways to keep your personal and business life safe from prying eyes.
We hope this expository text helped you and remember if you need any help you can always reach out to us in our live chat. We love assisting people in their pursuit of staying anonymous online.